Reporting on information supplied by whistleblower Edward Snowden, German magazine Der Spiegel last December revealed how the US National Security Agency (NSA) had successfully infiltrated an undersea telecommunications cable bundle linking Europe, North Africa, the Middle East and Asia. The revelation was one of the most disturbing of all the many disclosures from NSA documents supplied by Snowden, a former contractor for the agency now living in forced exile in Russia, and threatens to become the most politically controversial.
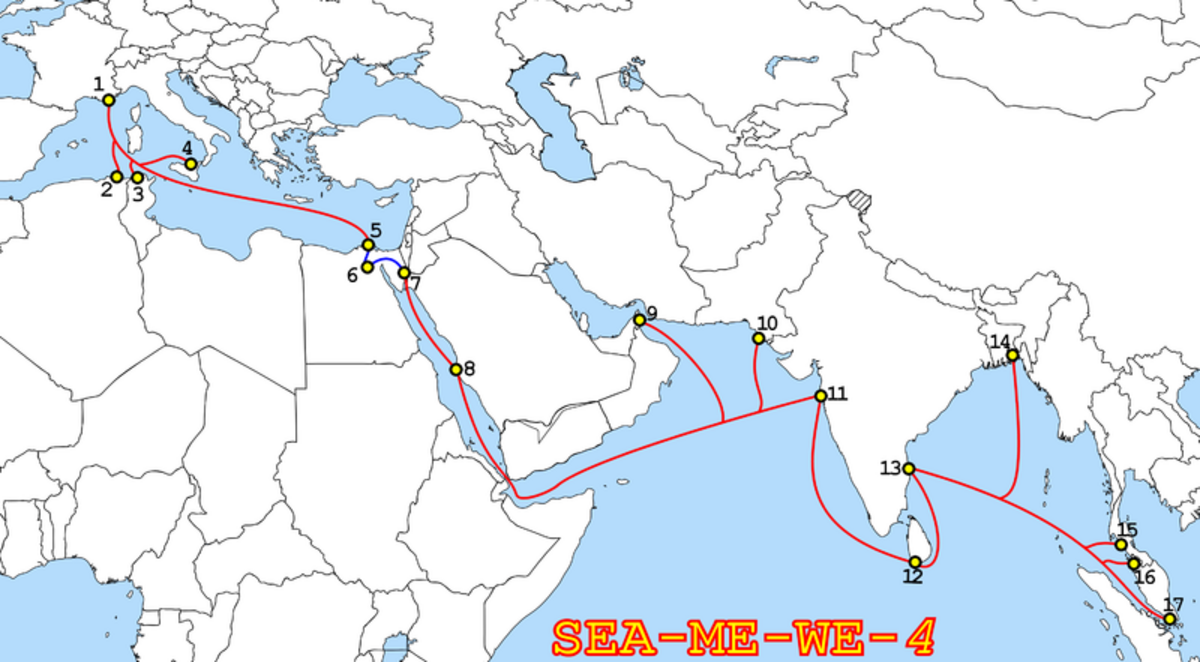
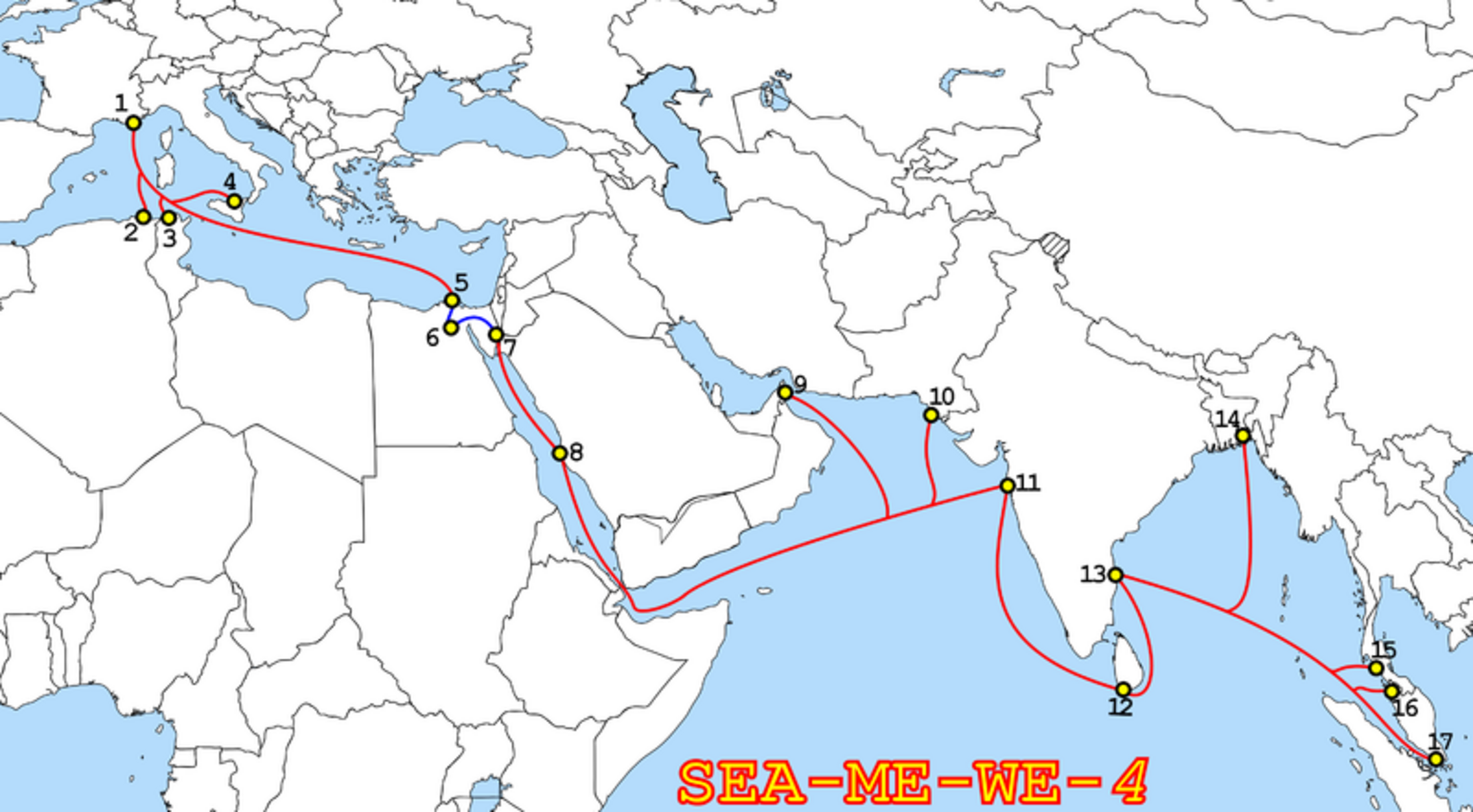
Der Spiegel cited NSA documents detailing how it had gained control of the SEA-ME-WE 4 undersea fibre optics cable system, which serves, among other things, as an important part of the skeleton of the worldwide internet. It runs from near the southern French city of Marseille, linking Europe with North Africa and the Gulf states, on to Pakistan and India, Bangladesh and finally through to Malaysia and Thailand.
On February 13th 2013, the NSA’s dedicated hacking unit, Tailored Access Operations, or TAO, “successfully collected network management information for the SEA-Me-We Undersea Cable Systems (SMW-4)”, reported Der Spiegel and quoting the agency’s own report on the matter. This allowed the NSA to “gain access to the consortium's management website”. Using a "website masquerade operation," the NSA was able to collect what it said was “Layer 2 network information that shows the circuit mapping for significant portions of the network.” TAO hacked an internal website of the cable operators, copying documents it contained on the technical infrastructure.
Enlargement : Illustration 1
These gave the NSA a total grip on the communications that passed through the submarine network, which is used by a consortium of 16 telecommunications operators, including France’s Orange (formerly France Telecom). Shortly after the revelations in Der Spiegel, Orange announced that it was to take legal action.
Under the French legal system, a complaint can be filed without targeting a specific organisation or person, a process that triggers a preliminary enquiry and which can then lead to a full-blown judicial investigation.

Contacted by Mediapart this week, a spokesperson for Orange said the French telecommunications giant will lodge its complaint against ‘persons unknown’ with the Paris public prosecutor’s office “in the coming days”. The company said its complaint cites “fraudulent access and presence into a system of automated data processing”, and “the as yet non-identified risks” involving “access to personal data (fraudulent collection and breach of the secrecy of correspondence)”.
The spokesperson, who underlined that Orange is a user and not manager of the cable network, said that it had asked the cable’s consortium “to carry out an audit of the internet site in question in order to determine precisely what had happened and, if need be, to reinforce security measures.”
The consortium and the individual national telecommunications operators who belong to it may well have to overhaul a major part of their networks. For the NSA attack revealed by Snowden is in reality but the tip of the iceberg; the most disturbing aspect of it is the method used by the NSA, based on a programme codenamed QUANTAM and which has significant geopolitical implications.
The TAO, the NSA’s specialised unit behind the attack, has a staff of ‘turned’ hackers recruited by the agency, which regularly attends hackers’ conferences. The documents supplied by Snowden and consulted by Der Spiegel detail the TAO’s activity of Computer Network Exploitation which targets computers, servers, routers, hardware firewalls, phones and SCADA systems (used to monitor and control industrial processes).
With its own R&D department, the TAO has developed a ‘toolbox’ for its surveillance operations, called QUANTUMTHEORY, and which has been supplied to the British signals intelligence centre at GCHQ. In an internal NSA presentation of the system, cited by Der Spiegel, the agency notes that "certain QUANTUM missions have a success rate of as high as 80%, where spam is less than 1%".
The magazine cited another internal NSA document entitled ‘QUANTUM CAPABILITIES’, and which listed as targets major web services including Yahoo, Facebook, Twitter and YouTube. According to the document, "NSA QUANTUM has the greatest success against Yahoo, Facebook and static IP addresses." Der Spiegel reported that it also reveals that only GCHQ was able to target Google users.
But the most impressive of the TAO’s Quantum programmes is QUANTUMINSERT, which appears to be what the NSA used to infiltrate the SEA-ME-WE 4 undersea fibre optics cable system. Last october, American IT security expert Bruce Schneier provided details of how the QUANTUM system works in an article for The Guardian newspaper published last October. In a report published last Novemlber, Der Spiegel revealed how QUANTUMINSERT had been used by GCHQ to infiltrate staff computers at Belgian telecommunications company Belgacom.
An 'adapted and perfected' system used by ECHELON
A QUANTUMINSERT operation begins with an investigation to identify a number of suitable targets who will serve as points of access for an attack. In the case of that against Belgacom, revealed in documents leaked by Snowden, GCHQ identified Belgacom employees working on network maintenance and security who used the professional networking site LinkedIn. GCHQ substituted their access to the real LinkedIn site by rerouting them to a fake one. When the targets connected to the fake site, their computers were infected with malware, via QUANTUMINSERT, which then gave the GCHQ hackers access into the Belgacom internal network.
The TAO also set up another infiltration system that enters a computer via the ‘error’ messages that can pop up when using the Microsoft Windows programme. The target’s computer is first identified by its IP address, which is entered into the NSA’s mass surveillance system called XKeyscore, which then monitors the targeted computer for whenever an ‘error’ message occurs. This contains key information on the computer’s security weaknesses, and which is stored and ready to be used in a future attack.
In its conception, this ‘man-in-the-middle’ technique, as it is dubbed, is nothing exceptional, but the methods used are far less conventional. To supplant a target’s chosen connection with a fake one, the NSA places its QUANTUM SERVERS at central points in the network, and which have a greater speed of connection. In practice, as soon as a target attempts to connect onto an internet site, one of the NSA servers will intercept the attempted connection first, infiltrating the computer with a programme that redirects the connection to a parallel network called FOXACID.
A tool used in many TAO attacks, FOXACID allows the NSA access to the very source of internet traffic, and in a largely undetectable manner. This is in part due to the fact that the strategic hubs of the internet network, called internet exchange points (IXPs), are situated in environments that are difficult to control.
An IT technician told Mediapart of a disturbing discovery made in 2011 at an IXP serving the United Arab Emirates and managed by the British company Epsilon Telecom. The IXP is hosted by a data center situated in Fujairah City, from where it manages a large part of traffic from the SEA-ME-WE 4 cable link which sends an 'arm' from its main course into Fujairah, geographically close to a US military base in Bahrain. When the technician went to inspect a routing table to check on the activity of a router, he found that some of the traffic had been diverted to a series of unusual addresses.
“We tried to find out how far back this went,” the technician, whose name is withheld, told Mediapart. “But when we realised that it was more than six months, the person in charge, who was British, told us not to look any further and to let no-one know.”
However, the technician continued with his research and discovered that an optic switcher, used to redirect traffic, had been placed on the SEA-ME-WE 4 cable. “Today, I have more and more the impression that it was a QUANTUM INSERT,” he said.
“’Network routers’ represent very sensitive equipment regarding the security of information systems”, warned French senator Jean-Marie Bockel, of the centre-right UDI party, in a 2012 report for the French Senate entitled ‘Cyberdefence: a worldwide challenge, a national priority’. “Indeed, nothing would stop a country that produces this type of equipment from placing within it a surveillance and interception mechanism, even a system that would allow for the interruption of all communications flows at any time,” Bockel underlined. “Placing such a surveillance mechanism directly into the heart of a ‘network router’ would make the mechanism ‘invisible’ and undetectable.”
Stéphane Bortzmeyer, an independent French IT engineer, said that before the latest revelations, specialists in the IT world were already aware of FOXACID “at least in the principle”, through information exchanged at conferences. “What is a real surprise,” said Bortzmeyer, “is the amplitude and the systemisation which required a lot of means.” Another network specialist, Kave Salamatian, from the University of Savoie, in eastern France, said the parallel network to where connections are diverted has been in existence since the ECHELON programme, a US-led worldwide signals and intelligence network (in which Britain, Canada, Australia and New Zealand also took part) and whose sophisticated eavesdropping activities were exposed in detail at the end of the 1990s. “At the time it was used to redirect intercepted communications,” said Salamatian, “but we haven’t reacted since ECHELON and this network appears to have been adapted and perfected.”
'First measure of security is not to feel secure'
In its attack on Belgacom, GCHQ managed to reach deep into the Belgian operator’s internal network and also the network of its subsidiary, BICS (jointly owned with Swisscom and South Africa's MTN). Once the British spying mechanism had entered the networks it was able to launch another programme, codenamed ‘Operation Socialist’, which decodes encrypted connections.
Concerning the submarine cable SEA-ME-WE 4, an investigation has yet to determine the extent of the NSA’s infiltration. It is already established that the infiltration was to be just the first stage of a much larger programme. “More operations are planned in the future to collect information about this and other cable systems,” wrote the NSA, as quoted by Der Spiegel from the documents supplied by Edward Snowden.
“I don’t know the architecture of their network, but it would be prudent to say that there is not much left that is kept from them,” said Stéphane Bortzmeyer. “They can do everything that it is theoretically possible to do.”
Kave Salamatian agreed. “You have a hand over the totality of the network and the capacity to do almost anything you want to,” he commented. “You can, for example, mount man-in-the-middle attacks at the very heart of the network to obtain logins.” Furthermore, if the attack is discovered and the internal network cleaned, there will always remain the ‘implants’, such as the servers and routers hacked by the NSA. “There needs to be a thorough audit of the SEA-ME-WE 4 cable,” added Salamatian. “But for that, there needs to be pressure from the clients. Now, some countries will always refuse.”
In his report on cyber defence, French Senator Jean-Marie Bockel envisaged but one danger; that of malware deliberately included in Chinese products sold to the West, which Bockel called for to be banned in France. “Today, given the amplitude of Edward Snowden’s revelations, I’ve somewhat changed my argument,” Bockel now says. “At the time [of the 2012 report], I had targeted the Chinese routers because they were in the news. But the Snowden affair has taken on a societal dimension. It is no longer only a question of technology.”
“In the beginning, I admit that I might have treated these revelations with a degree of light-heartedness,” Bockel added. “But today, we have gone beyond the limits of what is acceptable. The rules of the game must be placed back on the table.”
“I could say ‘yes’ to a boycott,” continued Bockel. “That would please a lot of people. But the reality is much more complex. We are in a situation of a dual-specific balance of power. The United States are our allies and friends. It must also be recognised that there is an exchange of information.”
However, he added that “this must not prevent us from showing our teeth”, and called for leading French and European IT companies to unite in building “an industry with sufficient weight” to be present in international negotiations. He also suggested the creation of a “UN-like” international convention that would establish the rules that must be abided for the protection of information. “Of course, there is a possibility that such a convention would not be respected, but Edward Snowden shows us that that would be made known.”
Kave Salamatian is less optimistic. “This affair demonstrates that there is a big problem,” he said. “We won’t get out of this if we don’t talk about it.” He underlined that every IT system can be hacked. “Today, it is no longer possible to place confidence in any of these tools,” he said. “There is therefore a job to do in mass education. The first measure of security is not to feel you are in security.”
Bortzmeyer concurred: “When the attacker is really determined, he can always break into a system. There are always gaps that can be exploited. It is just a question of time. Now, with the means at the disposal of the NSA…” He underlined that for a long time, security systems against attacks focussed only on ensuring the points of departure and arrival of information, and not what happens along the way. “You must always think as if there is a man-in-the-middle,” he warned.
“There are two types of attack,” Bortzmeyer continued. “Passive attacks, which consist of monitoring a communication and which generally go undiscovered, and the active attacks, in which the aim is to modify the information of the target. QUANTUMINSERT is situated between the two of them because it is made up of an active attack, then a passive attack. From a legal point of view, this could have consequences because here we are purely and simply in [the domain of] hacking.”
The imminent legal action to be launched by Orange over the “fraudulent” interception of communications running through the SEA-ME-WE 4 cable, and the internal audit of the network that it has called upon the operating consortium to make, may yet determine – notably if France launches a judicial investigation into the infiltration – what information was hacked by the NSA and to what extent the network was infiltrated.
Contacted by Mediapart, the French National Agency for the Security of Information systems (l’Agence nationale de la sécurité des systèmes d’information), refused to comment on the issue.
-------------------------
English version by Graham Tearse


