When the news broke the mainstream Russian media were delighted. On June 1st in interviews with first Associated Press then Russia Today, the director of the National Cybersecurity Agency of France (ANSSI), Guillaume Poupard, declared that there was no formal sign of Russian hackers being behind the so-called 'Macron Leaks'. This is the name given to the huge numbers of emails from Emmanuel Macron's campaign team that were leaked on the eve of his election as president of France on May 7th.
In his interviews Poupard made reference to a specific Russian hacking group which has close links to the Russian military's external intelligence agency the GRU. “Today I am absolutely unable to say that it is APT28 who were behind Macron leaks. I have absolutely no information to say if it's true or false,” he told AP.
He later told RT: “On the basis of technical elements that are too simple, it's not possible to say 'It's bound to be a state or it's clearly a criminal group'. It could be anyone.” ANSSI's boss added: “Given the simplicity employed it is conceivable that a single person could have done it and they could be in any country and have any motive.”

Enlargement : Illustration 1

Yet at the same time two separate investigations published by independent media in Russia told a different story. The online newspaper The Insider shed new light on the apparent involvement of a man called Georgy Petrovitch Roshka, whose name appears nine times in Cyrillic script in the metadata of some of the hacked emails in Macron Leaks. The website was able to show that, in all likelihood, he is someone who has worked with Russia's GRU.
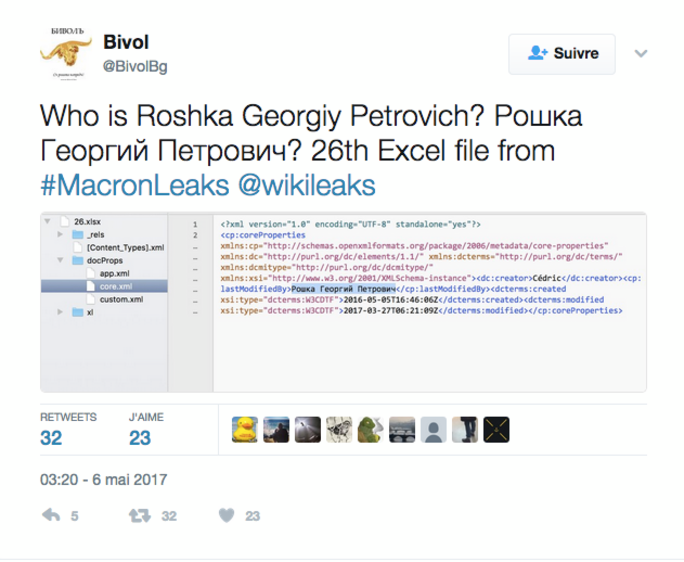
Enlargement : Illustration 2

As Mediapart has already reported (see here in French), this Russian 'fingerprint', which was left in rather an obvious manner, has puzzled many hackers. Mediapart's own investigation has already established that Georgy Petrovitch Roshka is indeed the name of a real person. A record of him was found at a renowned IT conference, Parallel Computational Technologies (PCT), which took place at Rostov-on-Don in southern Russia in April 2014.
At the time he was listed as an “expert” at a company called Evrika ('Eureka' in English), a major IT firm in Saint Petersburg. This organisation, which has around 700 people working for or with it, has obtained several licences from Russia's FSB – the successor to the KGB – authorising it to have “activities in the domain of protecting state secrets”, as for example the “detecting of electronic listening devices in engineering tools”. According to its website, regular clients include Russia's defence and foreign affairs ministries, Russian customs, the Federal Guard Service of the Russian Federation, Russia's central bank and the Russian public audit body.
When Mediapart contacted Evrika it responded with a convoluted email insisting that “for the period from January 1st, 2003 to May 10th, 2017” - details on dates that Mediapart did not ask for - Georgy Petrovitch Roshka “did not work [for the company] permanently and did not enter into a temporary contract”. A senior manager said that Georgy Petrovitch Roshka had also “taken part in the 2016 Parallel Computational Technologies (PCT) conference at Archangel and at the 2017 one at Kazan in 2017, describing himself as the employee of other organisations”.
But on the PCT conference website it has been impossible to find Roshka's name for the 2016 and 2017 events because the 'Who's Who' section is not available. The apparent reason for that has now been revealed. For once our initial article on the subject had been published Mediapart received a strange response from Professor Leonid Sokolinski who is one of the main organisers of the conferences, which take place under the authority of Russia's education and science ministry and which each year bring together hundreds of IT academics and specialists. The professor said that the detailed list of participants for 2016 and 2017 had disappeared “because of an error in the database that occurred on May 11th and which led to a loss of information”.
It was these supposedly deleted documents that the online news site The Insider obtained. They show that a Georgy Roshka was registered at the 2016 conference in Kazan as an associate of “Military Division Number 26165”. For the Archangel event this year he was put down as working with the “Centre for Strategic Studies”, a division of Russia's Ministry of Defence which openly recruits IT experts, programmers and hackers. These organisations eventually lead back to the GRU. Division 26165 is a unit based in Moscow which specialises in training professionals in cryptography, and is known as the GRU's 85th specialist centre.
The Insider has also confirmed through a source that Evrika itself has a centre for training future hackers. The Russian journalist Alexandra Garmazhapova managed to visit the centre incognito in August 2014. “The shutters in the room were down. The room was crammed with cables, computers and 'young talent' wandering around. You couldn't move around without being escorted. There are guards at the entrance, access codes and surveillance cameras inside,” she said.
In a separate investigation the Russian site Munscanner revealed that on February 9th, 2017, one of Evrika's founders, Alexandre Kinal, bought an apartment next to property belonging to Arkady Rotenberg, Nikolai Shamalov and Gennady Timchenko – three very close friends of Russian president Vladimir Putin – in a luxury building in Saint Petersburg that is guarded by state security guards.
One theory is that the name of Georgy Roshka was planted in the metadata deliberately to implicate Russians in the Macron Leaks affair, in what is known as a 'false flag' operation. However, to have done so the perpetrator would have required an astonishing knowledge of the mysteries of the Russian secret services. “In theory you could argue that someone introduced a Russian's data intentionally,” says Andrey Soldatov, a journalist on the Russian site Agentura.ru which covers security and intelligence issues. “As Vladimir Putin has said: 'Someone inserted a USB stick with the data of a Russian employee.' But it wasn't the name Felix Dzerzhinsky [editor's note, the first director of the forerunner to the KGB, the Cheka] that was found in the files but a credible name that's unknown to the wider public and that requires further investigation.”
At the opening of the Saint Petersburg International Economic Forum on June 1st, Vladimir Putin admitted that it was conceivable that Russian hackers had carried out attacks during the French elections. “Hackers are free people like artists. If artists get up in the morning feeling good, all they do all day is paint. The same goes for hackers. They got up today and read that something is going on internationally. If they are feeling patriotic they will start contributing, as they believe, to the justified fight against those speaking ill of Russia. Is that possible? In theory, yes,” said Putin, who nonetheless ruled out any state involvement. “At government level, we never engage in this. This is what is most important.”
While it is always very hard, if not outright impossible, to identify the culprit in cyber attacks, Emmanuel Macron's election campaign team had warned some months ago that they had been the target of hacking attempts. At the time it was suggested these attacks could be Russian in origin.
At the end of April the Japanese computer security firm Trend Micro published a very detailed report on the activities of 'Pawn Storm' - one of the other names for APT28, who are also known as 'Fancy Bear' and 'Guccifer 2.0' – an “active cyber espionage actor group” as they describe them. This GRU-linked group are strongly suspected of being behind the leak of Democratic Party emails in the United States in 2016 and of emails from the World Anti-Doping Agency. And in its April report Trend Micro revealed that the Macron campaign team's emails had come under attack from Pawn Storm.
In Paris the computer technology fraud squad the Brigade d'Enquêtes sur les Fraudes aux Technologies de l'Information (BEFTI) opened a formal investigation over the Macron Leaks affair on May 5th into “fraudulent access to an automated data processing system” and “violation of secret correspondence”. That investigation continues.
--------------------------------------------------------------------------------
- The French version of this article can be found here.
English version by Michael Streeter


